Fabric Setup for Azure AD DS LDAPS
This authentication setup must be done from the Management Center using Azure Active Directory Domain Services (Azure AD DS) via LDAP over SSL (LDAPS).
Carry out the following steps:
Prerequisites
A user must be set up so you can query the AD.
From your IT or AD administrator, you must get the following parameters:
- user & password
- user group
- admin_dn
- users_base_dn
- AD certificates in cer format and password as needed
Below is an example of such parameters:
- user: k2vfabric
- user password: Q1w2e3r4t5
- user group: K2vtdaadmin
- admin_dn:
CN=K2vtdaadmin,cn=users,DC=k2vfabric - users_base_dn:
CN=Users,DC=k2vfabric,DC=local - AD (LDAPS mode):
k2-fabric-ldap.k2vfabric.local - AD port: 636
Steps
The following steps must be carried out on all Fabric nodes by the root user:
- Update the /etc/hosts (if you cannot resolve the AD's DNS)
echo "10.21.1.134 k2-fabric-ldap.k2vfabric.local" >> /etc/hosts
Connect as fabric user
Update the admin_privileges file on one fabric node only (the one that you will start with first).
In this file, we will insert the name of the group that the user will use as the fabric admin, and the AD to which the user belongs. In our example K2vtdaadmin
cd $K2_HOME/
echo "K2vtdaadmin" > $K2_HOME/config/admin_privileges
- Config Fabric's config.ini file as follows:
cd $K2_HOME/
sed -i "s@#SERVER_AUTHENTICATOR=.*@SERVER_AUTHENTICATOR=adldap@" $K2_HOME/config/config.ini
sed -i "s@#url=.*@url=ldaps://k2-fabric-ldap.k2vfabric.local:636@" $K2_HOME/config/config.ini
sed -i "s@#admin_dn=.*@admin_dn=CN=K2vtdaadmin,cn=users,DC=k2vfabric,DC=local@" $K2_HOME/config/config.ini
sed -i "s@#admin_password=.*@admin_password=Q1w2e3r4t5@" $K2_HOME/config/config.ini
sed -i "s@#users_base_dn=.*@users_base_dn=CN=Users,DC=k2vfabric,DC=local@" $K2_HOME/config/config.ini
The following steps are unique to LDAPS (as opposed to LDAP):
- Import an LDAPS certificate to the Java truststore
- If Fabric is not hardened run the following:
keytool -importcert -file root_cer.cer -keystore apps/java/jre/lib/security/cacerts -alias "ldap"
- You will be prompted to enter a password. Use changeit
- When you are prompted for a confirmation, input yes
See this example:
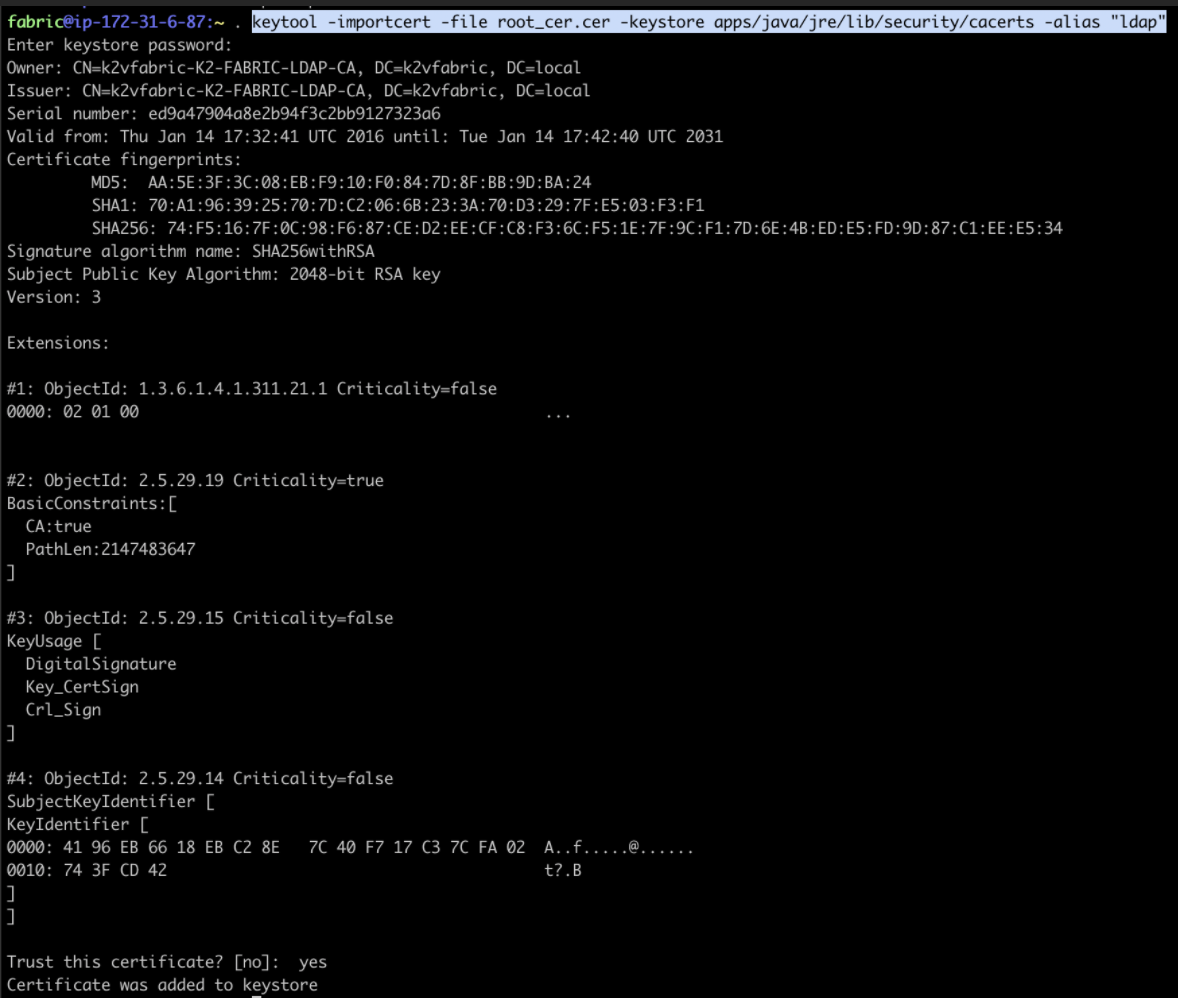
- If Fabric is hardened, run the following:
keytool -importcert -file root_cer.cer -keystore .cassandra_ssl/cassandra.truststore -alias "ldap"
- You will be prompted to enter a password. Use Q1w2e3r4t5
- When you are prompted for a confirmation, input yes
For more information about how Fabric works with LDAP, see here. For more information about SAML configuration in Fabric, please read here.
Fabric Setup for Azure AD DS LDAPS
This authentication setup must be done from the Management Center using Azure Active Directory Domain Services (Azure AD DS) via LDAP over SSL (LDAPS).
Carry out the following steps:
Prerequisites
A user must be set up so you can query the AD.
From your IT or AD administrator, you must get the following parameters:
- user & password
- user group
- admin_dn
- users_base_dn
- AD certificates in cer format and password as needed
Below is an example of such parameters:
- user: k2vfabric
- user password: Q1w2e3r4t5
- user group: K2vtdaadmin
- admin_dn:
CN=K2vtdaadmin,cn=users,DC=k2vfabric - users_base_dn:
CN=Users,DC=k2vfabric,DC=local - AD (LDAPS mode):
k2-fabric-ldap.k2vfabric.local - AD port: 636
Steps
The following steps must be carried out on all Fabric nodes by the root user:
- Update the /etc/hosts (if you cannot resolve the AD's DNS)
echo "10.21.1.134 k2-fabric-ldap.k2vfabric.local" >> /etc/hosts
Connect as fabric user
Update the admin_privileges file on one fabric node only (the one that you will start with first).
In this file, we will insert the name of the group that the user will use as the fabric admin, and the AD to which the user belongs. In our example K2vtdaadmin
cd $K2_HOME/
echo "K2vtdaadmin" > $K2_HOME/config/admin_privileges
- Config Fabric's config.ini file as follows:
cd $K2_HOME/
sed -i "s@#SERVER_AUTHENTICATOR=.*@SERVER_AUTHENTICATOR=adldap@" $K2_HOME/config/config.ini
sed -i "s@#url=.*@url=ldaps://k2-fabric-ldap.k2vfabric.local:636@" $K2_HOME/config/config.ini
sed -i "s@#admin_dn=.*@admin_dn=CN=K2vtdaadmin,cn=users,DC=k2vfabric,DC=local@" $K2_HOME/config/config.ini
sed -i "s@#admin_password=.*@admin_password=Q1w2e3r4t5@" $K2_HOME/config/config.ini
sed -i "s@#users_base_dn=.*@users_base_dn=CN=Users,DC=k2vfabric,DC=local@" $K2_HOME/config/config.ini
The following steps are unique to LDAPS (as opposed to LDAP):
- Import an LDAPS certificate to the Java truststore
- If Fabric is not hardened run the following:
keytool -importcert -file root_cer.cer -keystore apps/java/jre/lib/security/cacerts -alias "ldap"
- You will be prompted to enter a password. Use changeit
- When you are prompted for a confirmation, input yes
See this example:

- If Fabric is hardened, run the following:
keytool -importcert -file root_cer.cer -keystore .cassandra_ssl/cassandra.truststore -alias "ldap"
- You will be prompted to enter a password. Use Q1w2e3r4t5
- When you are prompted for a confirmation, input yes
For more information about how Fabric works with LDAP, see here. For more information about SAML configuration in Fabric, please read here.





