How Fabric Works With SAML
SAML can be used for the Fabric's Web Framework and its apps like Admin, TDM (7.1 and later) and DPM, where Fabric follows SAML standard flows.
Log in
Consider the following scenarios:
- A CRM user is logged into a system that acts as an identity provider, for example when the user logs in to his PC. The user wants to log in to Fabric by using a link from the organization's CRM.
- A support user is not logged into a system via an IDP (identity provider), e.g. he gets a ticket link via SMS, leading to a Fabric app.
In both cases, the SP (service provider) initiates an access flow:
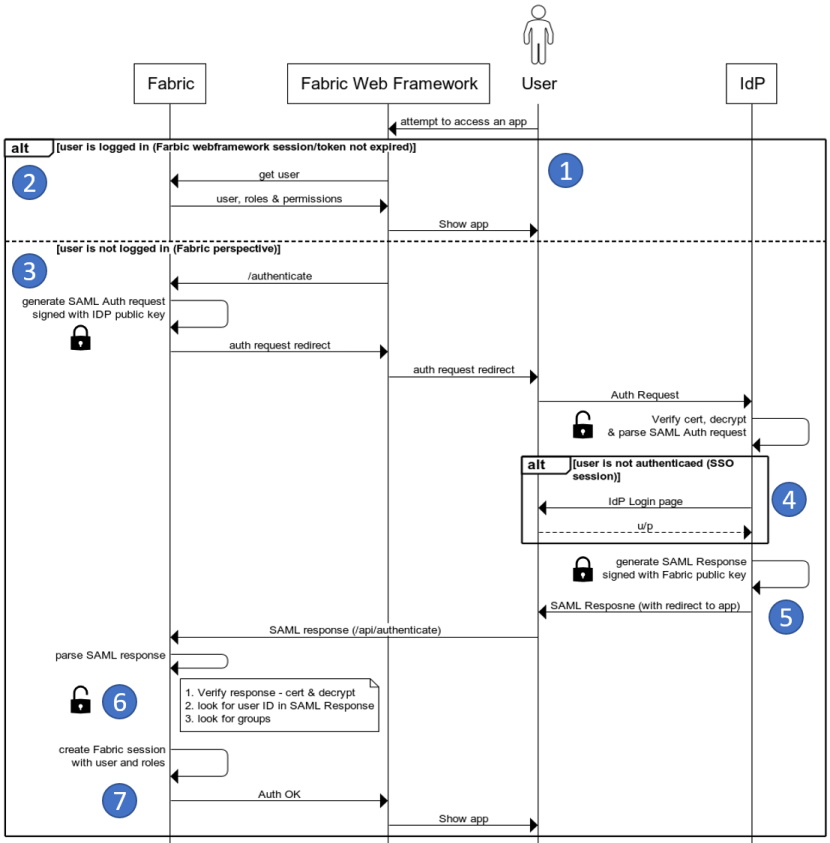
The user clicks on a link that leads him to a Fabric app (1 in the diagram below). One of two access methods follow:
a) If the user already has an existing Fabric session (2):
He is allowed access and can carry out actions according to the permissions granted to him by Fabric and its apps.
OR
b) If the user does not have an active session (3):
Fabric redirects him to the IDP, asking for authentication. This is the authentication request.
The user then either has an existing active browser session with the identity provider or establishes one by logging into the identity provider, via the IDP login page (4).
The identity provider builds the authentication response in the form of an XML-document containing the user’s identifier, signs it using an X.509 certificate and posts this information to Fabric, along with various other assertions and attributes (5).
Fabric verifies and opens the response, using the certification and encryption keys and algorithms. Fabric then processes and extracts the content, including the groups/roles that the user is associated with (6).
Fabric establishes a Fabric session for the user, enabling him access according to permissions granted to him by Fabric and its apps. The Fabric session provides (via the UsercCode) the information about the user and the roles that he is associated with (7).
Below is the logical flow illustrating these steps:
See here for more information about the user log-in process.
Log out and session expiration
If the user logs out, his Fabric session is invalidated. Similarly, after a period of time during which the user is idle, his Fabric session is terminated.
In both cases, Fabric starts the authentication process with the IDP, as explained in the Log In above (Step 3 in the diagram).
For more information and guidelines about setting up Fabric with SAML IDPs, refer to the examples for Azure AD SAML Setup Guide and Okta SAML Setup Guide. For more information about SAML configuration in Fabric, please see here.
How Fabric Works With SAML
SAML can be used for the Fabric's Web Framework and its apps like Admin, TDM (7.1 and later) and DPM, where Fabric follows SAML standard flows.
Log in
Consider the following scenarios:
- A CRM user is logged into a system that acts as an identity provider, for example when the user logs in to his PC. The user wants to log in to Fabric by using a link from the organization's CRM.
- A support user is not logged into a system via an IDP (identity provider), e.g. he gets a ticket link via SMS, leading to a Fabric app.
In both cases, the SP (service provider) initiates an access flow:
The user clicks on a link that leads him to a Fabric app (1 in the diagram below). One of two access methods follow:
a) If the user already has an existing Fabric session (2):
He is allowed access and can carry out actions according to the permissions granted to him by Fabric and its apps.
OR
b) If the user does not have an active session (3):
Fabric redirects him to the IDP, asking for authentication. This is the authentication request.
The user then either has an existing active browser session with the identity provider or establishes one by logging into the identity provider, via the IDP login page (4).
The identity provider builds the authentication response in the form of an XML-document containing the user’s identifier, signs it using an X.509 certificate and posts this information to Fabric, along with various other assertions and attributes (5).
Fabric verifies and opens the response, using the certification and encryption keys and algorithms. Fabric then processes and extracts the content, including the groups/roles that the user is associated with (6).
Fabric establishes a Fabric session for the user, enabling him access according to permissions granted to him by Fabric and its apps. The Fabric session provides (via the UsercCode) the information about the user and the roles that he is associated with (7).
Below is the logical flow illustrating these steps:

See here for more information about the user log-in process.
Log out and session expiration
If the user logs out, his Fabric session is invalidated. Similarly, after a period of time during which the user is idle, his Fabric session is terminated.
In both cases, Fabric starts the authentication process with the IDP, as explained in the Log In above (Step 3 in the diagram).
For more information and guidelines about setting up Fabric with SAML IDPs, refer to the examples for Azure AD SAML Setup Guide and Okta SAML Setup Guide. For more information about SAML configuration in Fabric, please see here.




