TDM Portal - Permission Groups (User Types)
There are three main types of TDM users, each with different permissions for different activities:
- Admin
- Owner
- Tester User
Each type is called a Permission Group.
All TDM windows can be accessed by all users in View mode. However, only authorized users with the relevant permissions can update TDM definitions.
Below are more detailed descriptions of the Permission Groups:
Admin
An Admin can execute all activities in the TDM Portal application.
Admins usually also define the TDM implementation in Fabric. They can execute all activities in the TDM Portal and are responsible for the following activities:
- Create, edit or delete systems.
- Create, edit or delete Business Entities and attach Logical Units or post-execution processes to each Business Entity.
- Create, edit or delete environments.
- Attach environment owners to each environment.
- Define permission sets in each environment and define permissions per permission set.
Owner
An Owner can be assigned to a specific TDM testing environment. Admins can define one or several Environment Owners for each testing environment.
Environment Owners can execute the following activities in their environment:
- Edit the environment details.
- Add or remove systems from the environment.
- Set environment variables.
- Create, edit or delete permission sets and define permissions per permission set.
- Attach users to TDM environment's permission sets.
Environment Owners cannot add or delete an environment and cannot add or remove Environment Owners from the environment.
Tester User
A Tester User can create and execute TDM tasks based on their TDM environment's permission set.
Permission Groups Mapping
How Does TDM Identify the User Type (Permission Group)?
The TDM Portal application is pre-integrated with Fabric Web Framework. The user logs into the Fabric Web Framework and Fabric authenticates the user. The TDM Portal application gets the user id and the user's Fabric roles from the user's session.
The users are defined and each user can be attached to one or several user groups in the organization.
The user groups are defined in the organization's service provider and must be defined in advance in Fabric as Fabric roles.
Our assumption is a one-to-one relation between a Fabric role and a user group in the organization's service provider.
Click for more information about Fabric's User Identification and Access Management.
The mapping of each Fabric role to a TDM Permission Group is done by the Permission Groups Mapping TDM window and is kept in the permission_groups_mapping TDM DB table.
The TDM Portal application identifies the user type (Permission Group) by its Fabric roles.
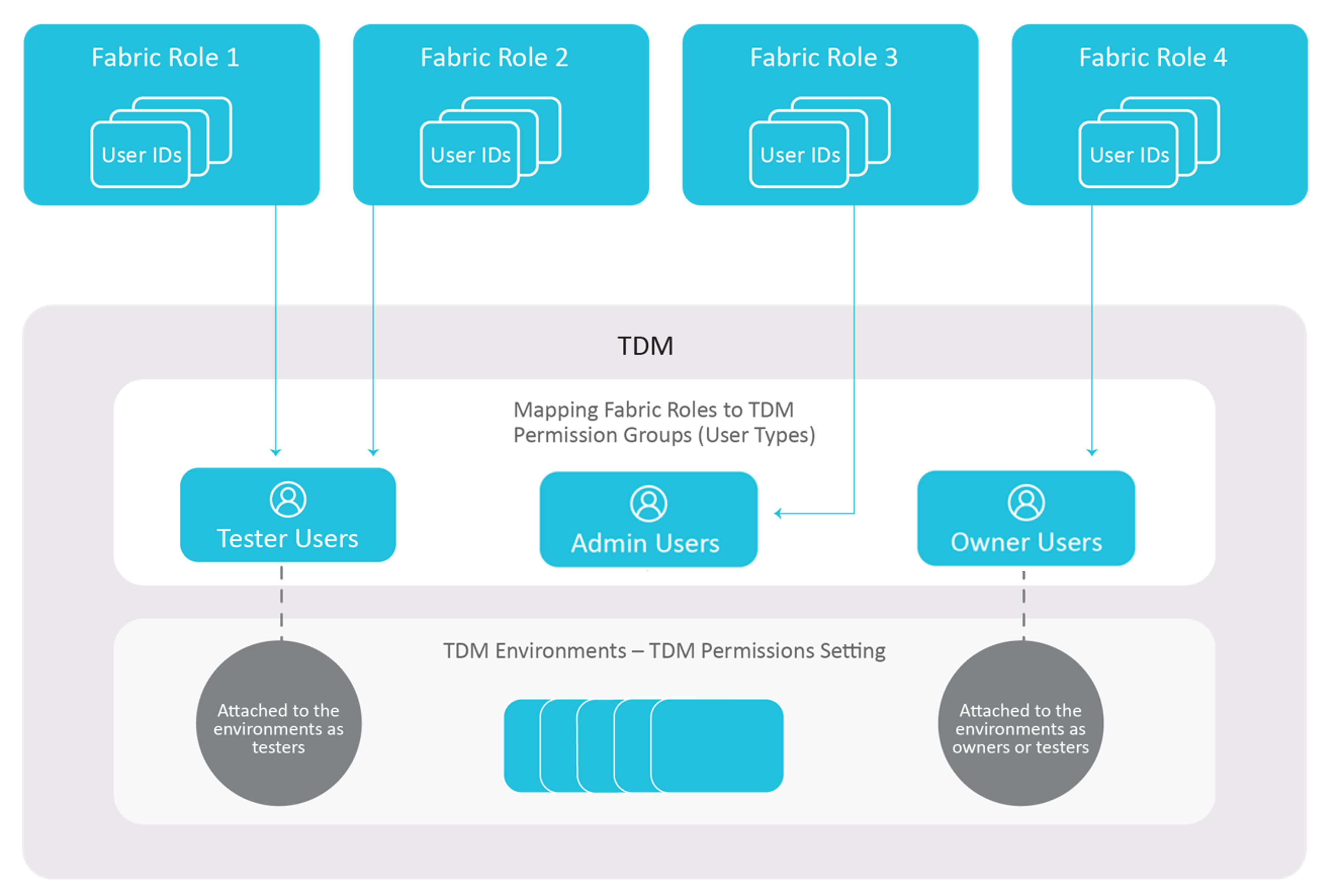
The following diagram illustrates the mapping between Fabric roles and TDM permission groups:
Example:
User id johnD123 is a tester and is attached to testers1 and testers2 Fabric roles.
User id clarkG is a tester and is attached to testers1 Fabric role.
User id janeR1 is a team leader and is attached to testingTeamLeaders Fabric role.
User leo10 is the TDM administrator and is attached to testingAdmin Fabric role.
Each group has a Fabric role with the same name as the Fabric role.
The testers1, testers2, testingTeamLeaders, and testingAdmin Fabric roles are mapped to TDM Permission Groups as follows:
| Fabric Role Name | TDM Permission Group |
| testers1 | Tester |
| testers2 | Tester |
| testingTeamLeaders | Owner |
| testingAdmin | Admin |
User id johnD123 logs into the Fabric Web Framework and is authenticated by Fabric. This user connects to the TDM Portal application.
The TDM gets the following attributes from the user session:
- User id: johnD123
- User's Fabric roles: testers1 and testers2.
The TDM checks the Permission Group of testers1 and testers2 Fabric roles. Their Permission Group is Tester.
Therefore johnD123 is a Tester user and is allowed to create and execute extract or load tasks on their TDM environments.
TDM Portal - Permission Groups (User Types)
There are three main types of TDM users, each with different permissions for different activities:
- Admin
- Owner
- Tester User
Each type is called a Permission Group.
All TDM windows can be accessed by all users in View mode. However, only authorized users with the relevant permissions can update TDM definitions.
Below are more detailed descriptions of the Permission Groups:
Admin
An Admin can execute all activities in the TDM Portal application.
Admins usually also define the TDM implementation in Fabric. They can execute all activities in the TDM Portal and are responsible for the following activities:
- Create, edit or delete systems.
- Create, edit or delete Business Entities and attach Logical Units or post-execution processes to each Business Entity.
- Create, edit or delete environments.
- Attach environment owners to each environment.
- Define permission sets in each environment and define permissions per permission set.
Owner
An Owner can be assigned to a specific TDM testing environment. Admins can define one or several Environment Owners for each testing environment.
Environment Owners can execute the following activities in their environment:
- Edit the environment details.
- Add or remove systems from the environment.
- Set environment variables.
- Create, edit or delete permission sets and define permissions per permission set.
- Attach users to TDM environment's permission sets.
Environment Owners cannot add or delete an environment and cannot add or remove Environment Owners from the environment.
Tester User
A Tester User can create and execute TDM tasks based on their TDM environment's permission set.
Permission Groups Mapping
How Does TDM Identify the User Type (Permission Group)?
The TDM Portal application is pre-integrated with Fabric Web Framework. The user logs into the Fabric Web Framework and Fabric authenticates the user. The TDM Portal application gets the user id and the user's Fabric roles from the user's session.
The users are defined and each user can be attached to one or several user groups in the organization.
The user groups are defined in the organization's service provider and must be defined in advance in Fabric as Fabric roles.
Our assumption is a one-to-one relation between a Fabric role and a user group in the organization's service provider.
Click for more information about Fabric's User Identification and Access Management.
The mapping of each Fabric role to a TDM Permission Group is done by the Permission Groups Mapping TDM window and is kept in the permission_groups_mapping TDM DB table.
The TDM Portal application identifies the user type (Permission Group) by its Fabric roles.
The following diagram illustrates the mapping between Fabric roles and TDM permission groups:

Example:
User id johnD123 is a tester and is attached to testers1 and testers2 Fabric roles.
User id clarkG is a tester and is attached to testers1 Fabric role.
User id janeR1 is a team leader and is attached to testingTeamLeaders Fabric role.
User leo10 is the TDM administrator and is attached to testingAdmin Fabric role.
Each group has a Fabric role with the same name as the Fabric role.
The testers1, testers2, testingTeamLeaders, and testingAdmin Fabric roles are mapped to TDM Permission Groups as follows:
| Fabric Role Name | TDM Permission Group |
| testers1 | Tester |
| testers2 | Tester |
| testingTeamLeaders | Owner |
| testingAdmin | Admin |
User id johnD123 logs into the Fabric Web Framework and is authenticated by Fabric. This user connects to the TDM Portal application.
The TDM gets the following attributes from the user session:
- User id: johnD123
- User's Fabric roles: testers1 and testers2.
The TDM checks the Permission Group of testers1 and testers2 Fabric roles. Their Permission Group is Tester.
Therefore johnD123 is a Tester user and is allowed to create and execute extract or load tasks on their TDM environments.





